We have many ways to run our automation in Azure. One of these options is the Azure Automation Account that has been there for a long time. However, that old trusty Automation Account is not as popular as other “modern” ways of running our automation - such as Azure Functions and CI/CD Pipelines. And I am also guilty of that. The main reason for me was the lack of the ability to use Managed Identity in Automation Accounts and having to use RunAs account instead.
Last year Microsoft brought System and User Assigned Managed Identities to Azure Automation account in a Public Preview, and we can now use it with our Automation Account Runbooks.
In this article, I will show you how to assign a Managed Identity to your existing Automation Accounts and how to change your Runbooks to authenticate using this new identity.
What is Azure Managed Identity?
Azure Managed Identity can be defined as a security identity object that can be used by an application or a resource in Azure to get access to specific Azure Resources.
There are two types of Azure Managed Identities, System-Assigned Managed Identity, and User-Assigned Managed Identity.
System-Assigned Managed Identity
System-Assigned Identity is enabled on Azure service, and it allows us to assign access to that service. In our case, this will be an identity assigned to our Automation Account.
User-Assigned Managed Identity
User-Assigned Identity is a stand-alone resource that we create as an identity within Azure AD. This same identity can be assigned to one or multiple Azure services.
Managed Identity vs. Run As Account
Run As Account is a service principal in Azure AD, and it can also be assigned a specific role. However, it relies on a certificate that needs to be renewed every one or two years. The advantage of Managed Identities is that they can self-manage this renewal without depending on the user to do that.
Use Managed Identity for your existing Automation Account and Runbooks
The good news is that we can now assign System or User-Assigned managed identity to our existing Automation Accounts.
Assign Managed Identity
Azure Portal:
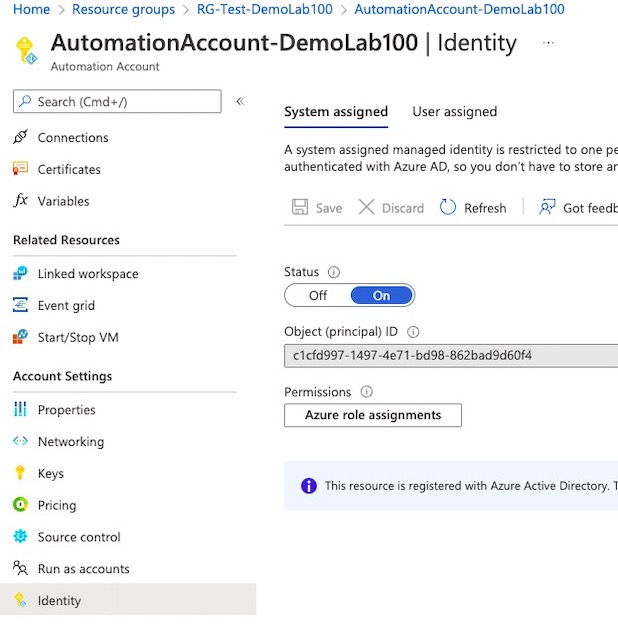
Go to Automation Accounts, select your account, go to Identity, and under the System Assigned tab switch Status to On.
PowerShell:
1
Set-AzAutomationAccount -ResourceGroupName $resourceGroupName -Name $automationAccountName -AssignSystemIdentity
Assign roles
Now that we have our identity, we need to assign a role.
Azure Portal:
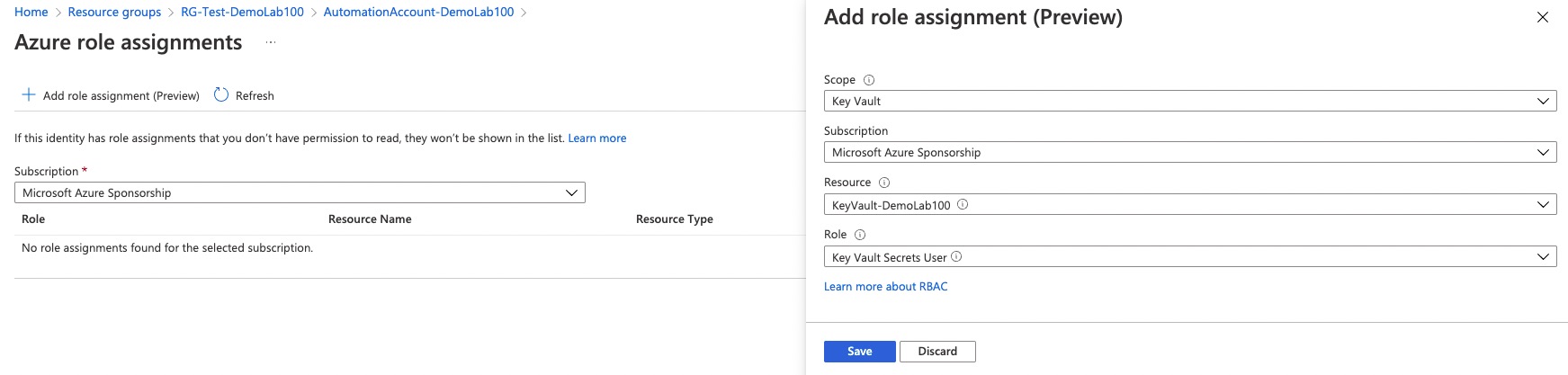
You can also assign roles at the same blade where you enabled System Assigned Managed Identity. Click on the Azure role assignments button and select scope and role.
PowerShell:
1
New-AzRoleAssignment -ObjectId (Get-AzADServicePrincipal -DisplayName $automationAccountName).id -RoleDefinitionName $roleName -Scope $scopeID
Update your Azure Automation Runbooks
Azure Automation Runbooks will now use a simplified way to authenticate against Azure.
Locate your runbooks and and replace the entire authentication part with the following code:
1
2
3
4
5
6
7
8
# Ensures you do not inherit an AzContext in your runbook
Disable-AzContextAutosave -Scope Process
# Connect to Azure with system-assigned managed identity
$AzureContext = (Connect-AzAccount -Identity).context
# Set and store context
$AzureContext = Set-AzContext -SubscriptionName $AzureContext.Subscription -DefaultProfile $AzureContext
Remove old Run As Accounts
Now that we have everything tested, we can remove old Run As Accounts.
Azure Portal
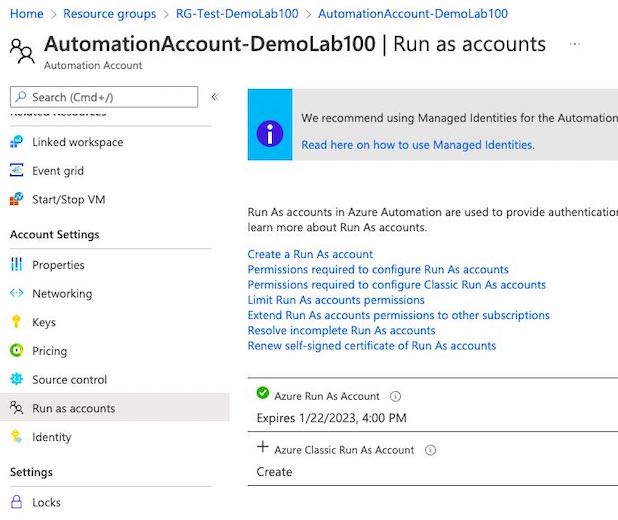
Go to Automation Accounts, select your Automation Account, go to the Run As Account section, select your account and click Delete button.
PowerShell:
1
2
3
4
5
6
7
8
#Remove RunAs Account Connection:
$RunAsAccountConnection = Get-AzAutomationConnection -ResourceGroupName $ResourceGroupName -AutomationAccountName $automationAccountName -Name AzureRunAsConnection
Remove-AzADApplication -ApplicationId $($RunAsAccountConnection.FieldDefinitionValues.ApplicationId)
#If you try to list service principals with the name of Automation Account, you will realize that there are multiple. System-Assigned Managed Identity will have the same name as the Automation Account. The Run As Account Service Principal starts with the same name, but it is longer. So you can search for the display name like this:
Get-AzADServicePrincipal | Where-Object DisplayName -like “$automationAccountName?*” | Remove-AzADServicePrincipal
Now you can remove Certificate renewal task from your maintenance calendars. In case you have any questions, feel free to reach out.
Thank you, and keep clouding around.
Vukašin Terzić
